 In the story of the Emperor’s New Clothes, the emperor parades before his subjects in his new “clothes,” yet no one dares to say that they do not see any suit of clothes on him for fear that they will seem “unwise.”
In the story of the Emperor’s New Clothes, the emperor parades before his subjects in his new “clothes,” yet no one dares to say that they do not see any suit of clothes on him for fear that they will seem “unwise.”
There’s a parallel in the security world today. Threat hunting for the purposes of breach prevention is not working. The industry is aware of this, yet no one is speaking up because it is difficult, and risky, to change the status quo and move in a new direction. As a result, we all continue down the same path, with the same threat hunting techniques, even when a better approach exists.
Case in point, during the “Stopping the Attacks” panel session at SecureWorld Boston the de facto standard of using breach detection and prevention to protect the organization was discussed in detail. Panelists espoused that organizations that take a proactive stance in automating network monitoring and processes, having the right controls in place, and establishing security benchmarks are in the best position to succeed with effective and timely breach response.
To be blunt, this threat hunting methodology is not working today. More, it will continue not to work, even though breach prevention security tools are getting more sophisticated every day.

A closer look why threat hunting for breach prevention doesn’t work
Why don’t these breach prevention solutions and threat hunting techniques work? Let’s look at the reasons why:
- Too much noise. We’ve said it before and we’ll say it again: InfoSec professionals must now respond to 5,000 intrusion alerts per day from their installed security tools. There is only so much manpower and hours in a day, making it impossible to investigate all of these security incidents.
Using this approach is essentially asking InfoSec to find the needle in the haystack, and even if they do, chances are good that it won’t be until weeks or months later – after the damage has been done.
- Cost and complexity. Traditional software tools can’t expand a hybrid network without incurring a lot of cost and complexity. Today’s organizations have IT infrastructures that are highly complex, dynamic, and scalable. More, they are comprised of networks, assets, and data, spanning and residing in a mix of on-prem servers, remote data centers, public clouds, and hybrid environments.
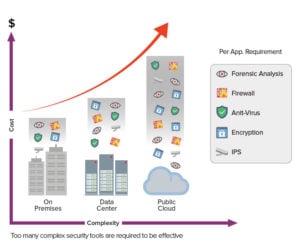 At the same time, most companies rely on a “stack” of discrete – siloed – security tools. While each is valuable in its own way, their lack of orchestration cannot provide the full security organizations require.
At the same time, most companies rely on a “stack” of discrete – siloed – security tools. While each is valuable in its own way, their lack of orchestration cannot provide the full security organizations require.
In addition, security tools become very costly, challenging, and complex to manage as an organization scales. Inevitably, it will take hours for highly skilled resources to properly configure, especially as they attempt to insert the desired level of automation and cloud deployment that often require additional costs for compute cycles.
- The need for SecDevOps. More companies are implementing the DevOps model to move their applications development efforts forward in a faster, more efficient manner. Yet securing a DevOps environment presents two challenges:
- Application developers do not have an easy set of tools to implement advanced security features, such as encryption or tokenization, during their normal build cycle.
- InfoSec resources are generally left out of the planning and development phases. So as the Ops team begins to test, the whole process can grind to a halt when InfoSec pushes back with valid concerns related to application vulnerability and risks to production-level data, which can include sensitive information, such as PII data.
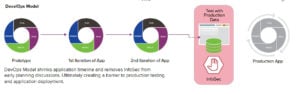
- Compliance consequences. Last but not least, we can’t forget about data privacy regulations and the need to maintain compliance. As stated above, it can take months, if not years, to identify, investigate, and fully understand the impact of a breach. Yet organizations can’t afford to take this long – in the case of the European Union’s GDPR regulation, companies have just 72 hours to report a breach.
Make breaches irrelevant
Set against this backdrop, it should be obvious that a new approach is needed when it comes to protecting your assets. At ARIA Cybersecurity Solutions, we believe that the better strategy is to make breaches irrelevant.
Why? On one hand, cyber-attacks continue to rise. The number of data breaches in the U.S. jumped 29 percent in the first half of 2017, hitting a record high of 791 (according to a report from the Identity Theft Resource Center and CyberScout, the data risk management company.
As a result, approximately 12 million records were exposed in these 791 breaches. These stolen records include banking information, credit card numbers, medical files, Social Security numbers, and other confidential data. And odds are that 12 million is just the tip of the iceberg.
ARIA Cybersecurity Solutions are optimized to tackle the complexity of data breaches by. Our solutions:
- Automatically identify and notify of breaches as they are occurring
- Provide detailed reporting needed to immediately begin a focused breach investigation, and complete it in hours
- Provide simple connectors for application developers to apply advanced security features during the development phase
- Apply the appropriate security policies to VMs and containers as they spawn, to best protect the data and applications within them
Interested in learning more, and what makes ARIA Cybersecurity Solutions different? Download our white paper, “How to Secure DevOps Across Any Environment,” view any one of our on-demand webinars, or contact us today.
